Understanding Crypto Bounties
A. What is a Crypto Bounty?
Crypto bounty represent rewards offered in digital assets for specific tasks or contributions within the crypto space. It’s one of the smart ways to earn cryptocurrencies without an investment. Crypto Bounty serve as incentives to encourage participation, ranging from bug hunting and marketing to development and translation.
Crypto bounties are different from Initial Coin Offerings (ICOs) in certain factors.
| Aspect | Crypto Bounty | ICO (Initial Coin Offering) |
| Purpose | Incentivize contributions, tasks, and engagement. | Fundraising for new cryptocurrency projects. |
| Rewards/Investment | Participants earn tokens as rewards for completing tasks. | Participants invest money to purchase project tokens. |
| Role | Participants contribute time and effort for rewards. | Participants become investors in the project. |
| Risk | Involves effort, minimal financial risk. | Involves financial investment with potential market risks. |
| Regulation | Less regulatory scrutiny as it’s task-based. | Increased regulatory oversight due to investment nature. |
B. Brief History and Evolution
The genesis of crypto bounties traces back to the early days of Bitcoin, where community-driven initiatives rewarded individuals for identifying bugs and contributing to the ecosystem. Over time, these initiatives evolved into diverse programs across various crypto projects and platforms.
C. Importance and Role in the Cryptocurrency Space
Crypto bounties play a pivotal role in fostering engagement and growth within the cryptocurrency sphere. They incentivize talent, foster innovation, and enhance security by harnessing the collective efforts of a global community towards advancing blockchain technology and its applications.
Types of Crypto Bounties
1. Bug Bounties
Bug bounties focus on identifying and reporting vulnerabilities or bugs within a cryptocurrency project’s code or platform. Rewards are often offered based on the severity of the discovered issue.
2. Marketing Bounties
Marketing bounties involve promotional activities such as social media sharing, content creation, or community engagement to increase awareness and adoption of a crypto project.
3. Development Bounties
Development bounties are tasks related to coding, programming, or enhancing the functionalities of a blockchain project or its associated applications.
4. Translation Bounties
Translation bounties revolve around translating project-related content, such as whitepapers, websites, or documents, into different languages to reach a broader audience.
5. Others (if applicable)
Depending on the project’s needs, there might be additional bounty categories such as design, testing, or user experience (UX) improvement tasks.
How Do Crypto Bounties Work?

1.Bounty Platforms and Websites
These bounties are often hosted on specialized platforms or websites dedicated to connecting bounty hosts with bounty hunters. These platforms act as intermediaries, facilitating the bounty creation, submission, and reward distribution processes.
2.Bounty Hosts
Individuals
They could be entrepreneurs, enthusiasts, or developers seeking to promote their innovations or ideas within the crypto community. These individuals often utilize bounty programs to attract attention, generate buzz, or encourage community involvement. Their bounties may range from simple tasks like social media promotion to more complex activities such as coding or content creation.
Companies/Projects
- Companies and established projects use bounties as a strategic tool to crowdsource tasks, tap into the collective expertise of the community, or expand their project’s reach.
- Tasks includes bug identification, marketing efforts, or development tasks to leverage the collective skills of the community.
3.Bounty Hunters
Bounty hunters are diverse individuals with varied skill sets who actively participate in bounty campaigns. They come from different corners of the world and contribute their expertise to complete tasks outlined by bounty hosts.
These hunters play a pivotal role in the success of bounty programs, offering their skills in areas like software development, marketing, community engagement, design, writing, and more. They are essentially freelancers within the crypto landscape, seeking opportunities to contribute and earn rewards in the form of cryptocurrencies or tokens.
Process Flow – From Creation to Reward Distribution
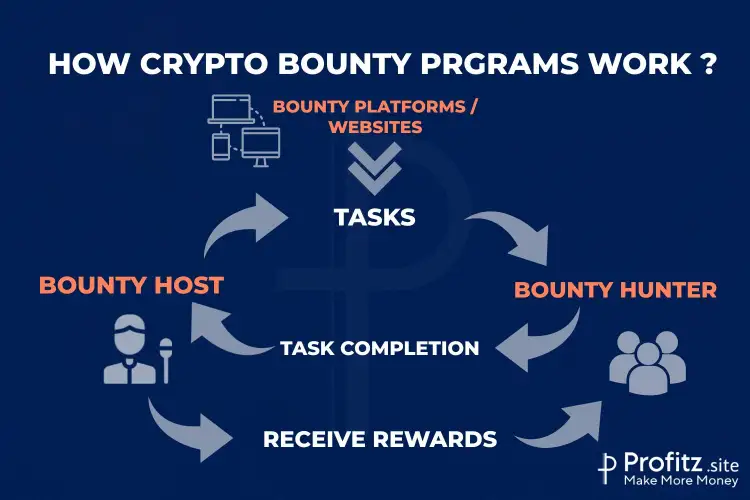
- The bounty creation process starts with a host defining the tasks, specifying the rules, and determining the rewards for completion.
- Once posted, bounty hunters select tasks, complete them, and submit their work according to the guidelines provided.
- The host then reviews submissions, assigns rewards based on the quality and accuracy of the completed tasks, and distributes the corresponding cryptocurrency rewards to the participants.
Advantages & Risks
Advantages for Hosts
Increased Engagement: Bounty campaigns attract a broader audience, driving higher engagement and interest in the project or product.
Cost-Efficiency: By leveraging the skills of the community, hosts can accomplish tasks at a fraction of the cost compared to traditional methods.
Diverse Skill Sets: Access to a pool of diverse talents allows hosts to tap into various expertise areas, enhancing the project’s quality and reach.
Marketing Amplification: Bounty programs serve as effective marketing tools, spreading awareness about the project through word-of-mouth and social media.
Advantages for Hunters
Earning Opportunities: Bounty hunters have the chance to earn cryptocurrencies or tokens by completing tasks, providing a source of income within the crypto space.
Skill Enhancement: Participation in diverse bounty campaigns helps hunters refine existing skills and develop new ones, fostering personal and professional growth.
Access to Projects: Hunters gain access to upcoming projects and innovations within the crypto industry, enabling early involvement and potential future opportunities.
Flexibility and Autonomy: Bounty hunting allows individuals to work on tasks of their choosing, offering flexibility in working hours and location.
Challenges Faced by Both Parties
1. Security Risks
Vulnerabilities: Hosts may face risks associated with disclosing project details, leading to potential exploitation or security breaches.
Phishing and Scams: Hunters are susceptible to fraudulent bounty campaigns that aim to deceive and steal personal information or exploit their work without proper compensation.
2. Trust Issues
Credibility Concerns: Hosts might struggle to establish credibility, leading to a lack of trust among potential hunters.
Payment Reliability: Hunters face uncertainties regarding timely and fair compensation, leading to distrust towards certain hosts or platforms.
3. Payment Concerns
Delayed Payments: Hosts may face challenges in distributing rewards promptly due to various reasons, affecting hunters’ trust and motivation.
Value Fluctuations: Cryptocurrency price volatility can impact the value of rewards received, causing discrepancies between expected and actual earnings for hunters.
How to Participate in Crypto Bounties
Finding and Choosing Bounties
Platforms and Websites
There’s a plethora of platforms and websites dedicated to hosting crypto bounty programs. These serve as treasure troves for bounty hunters seeking opportunities.
Platforms like Bitcointalk, Bounty0x, and Reddit’s bounty threads are popular hubs where hosts list their campaigns. Each platform has its interface and layout, offering diverse bounties across bug identification, marketing, development, and more.
Evaluating Legitimacy of the specific bounty program is crucial for safety & success (will be discussed in detail later)
Several platforms and marketplaces facilitate the creation and management of crypto bounties. These platforms act as intermediaries, connecting bounty issuers with participants. Some well-known platforms include:
- Gitcoin: A platform specifically designed for Ethereum-based projects, Gitcoin enables the creation of bounties for tasks ranging from coding to community engagement.
- Bounty0x: This decentralized bounty hunting network supports a wide range of tasks and is not limited to any particular blockchain. It allows users to create and fulfill bounties using smart contracts.
- Coinbase Earn: While not a traditional bounty platform, Coinbase Earn offers users the opportunity to earn various cryptocurrencies by participating in educational tasks and tutorials.
Steps to Participate
Registration and Account Creation
To participate in a bounty, registering on the respective platform is the initial step. Create an account, providing accurate information. Some platforms may require additional verification steps, such as linking social media accounts or completing Know Your Customer (KYC) procedures for security purposes.
Selecting and Completing Tasks
Once registered, browse through the available bounties. Select tasks aligned with your skills and interests. Read the bounty requirements thoroughly. Whether it’s identifying bugs, creating content, or marketing initiatives, follow the instructions diligently. Completing tasks accurately and within the specified timeframe increases the likelihood of receiving rewards.
Submission Process
Submission is a critical phase. Ensure adherence to all requirements outlined in the bounty. Submit your work through the designated channels within the stipulated timeframe. Accuracy, quality, and compliance with the bounty guidelines significantly impact the chances of reward approval.
Tips for Success in Bounty Hunting
Specialize and Diversify
Specializing in specific bounty types based on your expertise can increase efficiency. However, diversifying your participation across various types of bounties can expand opportunities for earning rewards.
Engage and Network
Active participation in forums and discussions related to crypto bounties can provide insights, tips, and new opportunities. Engaging with the community fosters networking, potentially leading to additional bounty leads or collaborations.
Stay Updated
The crypto landscape evolves rapidly. Stay abreast of new bounty releases, changes in platforms’ guidelines, and emerging trends. Timely updates can offer a competitive edge in securing lucrative bounty opportunities.
Best Practices and Safety Measures
Protecting Personal Information
Minimize Disclosure: Bounty hunters should exercise caution when providing personal details on bounty platforms or to hosts. Revealing sensitive information, such as private keys or personal identification, can pose significant risks. It’s prudent to share only necessary information required for the completion of tasks.
Use Secure Channels: When communicating with hosts or engaging in bounty-related activities, using secure channels is essential. Utilizing encrypted messaging platforms or secure email services adds an extra layer of protection against potential data breaches or unauthorized access.
Verifying Legitimate Bounties
Research and Due Diligence: Before participating in a bounty campaign, conducting thorough research about the host, their project, and the credibility of the bounty platform is imperative. Looking for reviews, checking community feedback, and verifying the authenticity of the project can help identify genuine opportunities.
Scrutinize Task Requirements: Legitimate bounty campaigns have clear, reasonable tasks aligned with the project’s goals. Beware of campaigns with vague or overly complicated tasks, as they might be attempts to exploit hunters for malicious purposes.
Ensuring Secure Transactions
In the crypto bounty landscape, ensuring secure transactions is vital to protect assets and prevent unauthorized access to funds.
Use Secure Wallets: Bounty rewards are often distributed in cryptocurrencies or tokens. Using reputable, secure wallets to receive and store these rewards is essential. Hardware wallets ( Trezor, Ledger, Billfodl from Privacypros ) or reputable software wallets ( Exodus, Trust wallet ) with robust security features can safeguard against theft or hacking attempts.
Verify Payment Addresses: Before providing any payment details, verify the authenticity of the payment addresses provided by hosts. Malicious actors may attempt to deceive hunters by providing fraudulent wallet addresses, leading to loss of funds. Choose your Crypto exchange wisely. Here you can see reviews of best Crypto exchanges.
Success Stories and Case Studies
Notable Examples of Successful Bounty Campaigns
1. Bug Bounty Programs: Companies like Google, Facebook, and Microsoft have successfully run bug bounty programs, encouraging ethical hackers to find and report vulnerabilities in their systems. These programs have led to the identification and resolution of critical security issues, enhancing the overall safety of these platforms.
2. Blockchain Projects: Ethereum’s early adoption of bounty programs incentivized developers to find and fix bugs in its smart contract code. These initiatives helped fortify the platform’s security and reliability, contributing to its robustness in the decentralized ecosystem.
Ethereum Bug Bounty Program
Ethereum, the pioneering smart contract platform, has run a successful bug bounty program since its early days. This program has been instrumental in identifying and resolving vulnerabilities in the Ethereum protocol. The Ethereum Foundation collaborates with platforms like Gitcoin to organize and manage these bounties, fostering a culture of security within the community.
Binance Hacker Bounty
In 2019, Binance, one of the world’s largest cryptocurrency exchanges, fell victim to a security breach. To address the situation proactively, Binance announced a hacker bounty, offering a substantial reward for information leading to the identification and arrest of the individuals responsible. This approach not only incentivized the community to assist in resolving the issue but also showcased transparency and accountability on Binance’s part.
3. Marketing and Community Building: ICOs (Initial Coin Offerings) often leverage bounty programs for marketing purposes. Projects like Stellar used bounties to encourage social media sharing, content creation, and community engagement, fostering a widespread and enthusiastic community around their token.
Recap of Key Takeaways
- Crypto Bounty programs comprises the triad of bounty hosts, hunters, and platforms.
- Hosts initiate bounty campaigns, leveraging the collective skills of hunters who actively participate to complete tasks for rewards.
- Platforms serve as the bridge, facilitating seamless interactions between hosts and hunters, ensuring transparency, and streamlining the bounty process.
- What you can do? Apart from geographics & skills you have, Go & explore various Crypto bounty programs, Choose the best that suits you & start earning Crypto coins.
Before concluding here are some ways to earn FREE crypto currencies. Some ways are Airdrops, Crypto Faucets, Crypto Yield Farming. You can earn Crypto Currencies just by exchanging coins – It’s called Arbitrage.
If you want to get your own Cryptocurrency you can do Crypto mining. You can even do Crypto mining in your smartphone.
You can earn Cryptocurrencies by all the above ways.
Happy Earning Crypto !!!
